how do you ensure privacy in this day and age https://forums.funtoo.org/topic/3025-how-do-you-ensure-privacy-in-this-day-and-age/
#privacy #funtoo #thread #age
interesting, win10 during setup tells you “create a super memorable password”, doesn’t tell “create a super unbrutforcable password” or something more security oriented. because super memorable is an alias to easily breakable, right? probably. (:
#microsoft #security #password #windows10 #usability #privacy
https://puri.sm/shop/librem-5/
runs #debian, not clear about window manager/desktop environment.
let’s see if it gathers community. #linux #phone #privacy #surveillance #matrix #decentralization
would like to write about protonmail.ch or protonmail.com
It might look like I am criticizing the project, while I do not. Apparently I have even donated them money.
Recently they’ve opened free registration, so you can get your protonmail.com address. Actually I do not understand why sometimes you get protonmail.com and sometimes protonmail.ch domain. Your username @ protonmail.com does not work as username@protonmail.ch and vice versa.
So, protonmail claims that they encrypt your mailbox, and only you can decrypt it. You need to have two passwords - first for the login, and second to decrypt the mailbox. If you happen to forget the second password, then your mailbox will be lost forever, you can create a new mailbox and encrypt it with different password.
It all seems very attractive, however there are questions:
— if the mailbox is encrypted, then when you receive the email, they cannot put it to the mailbox? Then they have to store it at some temporary location? Wait until you login to decrypt the mailbox, so that they can add the email to that mailbox while it’s temporarily decrypted?
— if there is such a state, then if they required to retrieve your emails, they can do that technically, when you are logged in? and when you are not logged in, they can make copies (again, technically) of your emails while they were not added to your mailbox?
— if you send emails to the other email provider, like google, then obviously, your email will be stored and never erased by google. that is why Protonmail suggests to send emails from proton to proton in order to stay safe.
#protonmail #mail #security #cryptography #privacy
here was a ted talk, i believe, and one guy from Sweden was saying - if somebody is watching me, i would prefer it to be local NSA, rather than US NSA.
Well, I envy him. He trusts local NSA so much. He believes that it’s not engaged in crime, corruption, unlawful activities. At least, it’s likely engaged less than the NSA of my country. Thus he feels himself more confident than me.
I am afraid of my local NSA more than of wolves, vampires, ghosts. It’s not they who might nock my door at 5am, when I am completely innocent. And definitely not US NSA. It’s my native, lovely, NSA. Which supposedly defends interests of the nation, but I am not quite sure it does not actually defend interests of other parties like their own, government, criminals instead. Sigh.
#safety #naive #sweden #nsa #privacy #surveillance #corruption #crime #confidence #security #freedom
i had a drive failure recently. not an issue since i have a backup. mostly my photos, some docs, i don’t remember what was there. i only did not have time to backup a couple of directories with photos of that day. and there was one picture which wasn’t bad, photo of a couple and i know they would be glad to get it. that’s why i fired photorec to recover files.
what’s interesting, is that i get many images i don’t remember about. then i understood that they come from the home directory backup i kept on that drive. and here it is, all my browsing history in a palm. all my interests, sites i have visited, everything in pictures from my browser cache. and it became very clear to me, that if i were logged in to google or facebook, they would have this too.
#privacy #surveillance
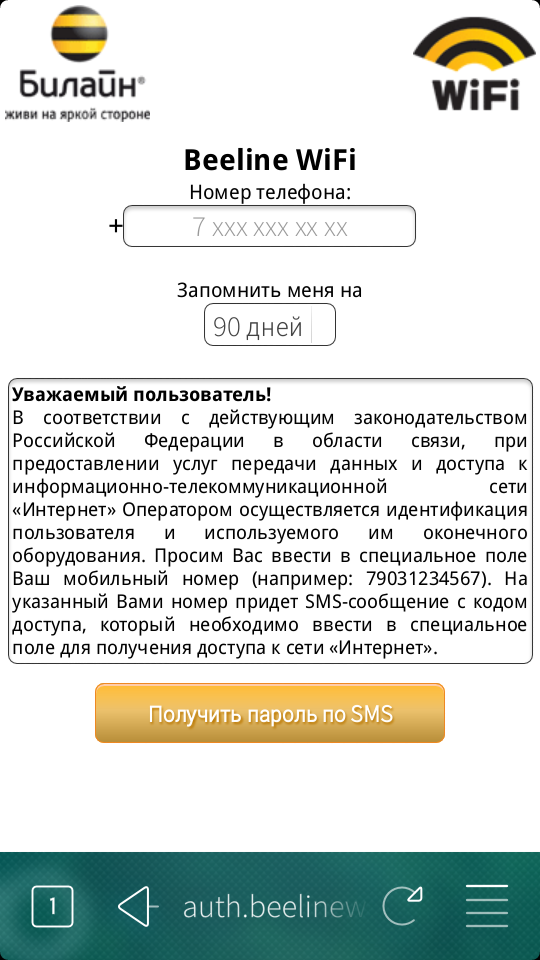
according to the new russian law, free wifi providers should gather information about those who use their wifi. in this particular case, access point at starbucks demands a phone number to send sms to it with code, which needs to be entered to that form in order to get internet connection. i. e. identification via phone number, and in orderbto get a phone number one has to provide passport information.
#anonymity #internet #russia #screenshot #surveillance #law #privacy #freedom
one guy from sweden, i believe, said in a talk (may be ted) related to surveillance, that if someone has to spy on him, he prefers it to be sweden service, not foreign.
well, amusing europeans. (: your secret services did not behave like kgb, and did not kill or send to siberia batches of people for the wrong word or even for nothing. of course you would prefer surveillance of your own state.
#privacy #surveillance #patriotism #freedom
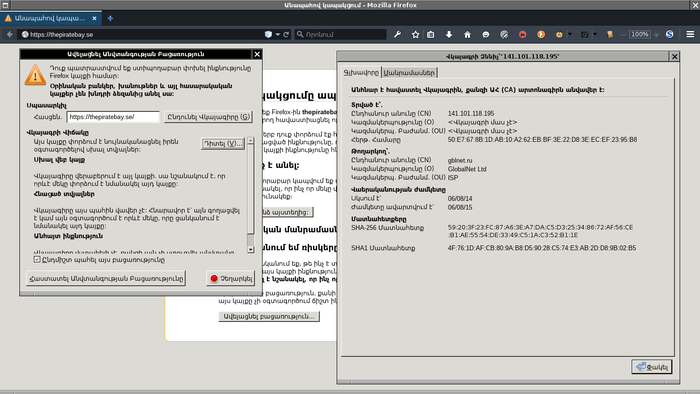
connecting to the piratebay from my hotel wifi. it asks to accept a self signed certificate issued by gibnet.ru. of course i did not, instead, via tor it did not require to accept any unknown certificate. if i would accept it they would be able to intercept my traffic. (:
#russia #security #privacy #thepiratebay #ssl #https #crypto #intercept #screenshot #freedom
#եսնորեկեմ #բարեւ
#newhere #hey
@{ Hay Dude ; haydude@spyurk.am} Ուր 28 Մար 2014 01:18:24 AMT
Hay Dude ; haydude@spyurk.am} Ուր 28 Մար 2014 01:18:24 AMT
Hay I’m a dude! I’m into all kinds of things, among them (Dat Da Daaaa!):
#armenia (of course!) #art #poetry #literature #music #dancing #EDM #jazz #coding #opensource #geekery #privacy #anonymity #NWO #NSA #NewSSR #UFOs #cats #tantra #dharma #FirstNations #witchery #toltec #shamanism
I’m so easy to talk to it’s like talking to yourself (I’m told LOL), so get at me! <3
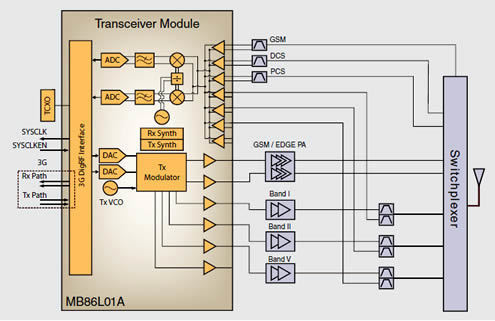
The second operating system hiding in every mobile phone
I’ve always known this, and I’m sure most of you do too, but we never really talk about it. Every smartphone or other device with mobile communications capability (e.g. 3G or LTE) actually runs not one, but two operating systems. Aside from the operating system that we as end-users see (Android, iOS, PalmOS), it also runs a small operating system that manages everything related to radio
http://www.osnews.com/story/27416/The_second_operating_system_hiding_in_every_mobile_phone
#surveillance #mobile #operating-systems #android #ios #palmos #3g #gsm #lte #technologies #radio #smartphones #device #communications #privacy #freedom
New edition of Wirth’s book Project Oberon is out. It describes not only built from scratch software(entire operating system and compiler), but design of the hardware as well.
The vast complexity of popular operating systems makes them not only obscure, but also provides opportunities for “back doors”. They allow external agents to introduce spies and devils unnoticed by the user, making the system attackable and corruptible. The only safe remedy is to build a safe system anew from scratch.
http://www.inf.ethz.ch/personal/wirth/ProjectOberon/index.html
#oberon #wirth #niklaus-wirth #risc #programming #fpga #books #programming-languages #compilers #operating-systems #compiler #freedom #design #security #privacy #surveillance #reliability
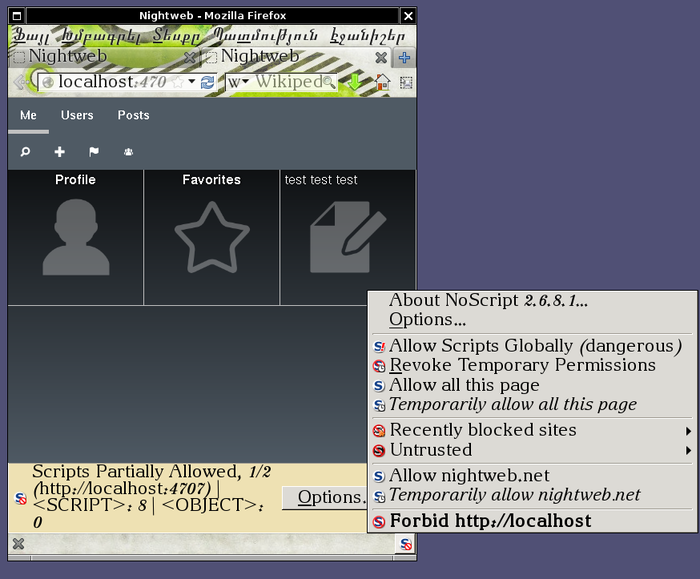
am I right that #nightweb is using #java-script loaded from nightweb.net? Then if nightweb.net gets hacked all the clients will be affected. Would like it to load #js locally, from the local file system.
#security #privacy #net #internet

#Lavabit’s founder offered to write the code to #tap #Snowden ’s #email metadata. The #government balked at the cost: $3500
https://twitter.com/csoghoian/status/385805573574230016
#surveillance #privacy #internet
Aside of using #amazon, #joindiaspora uses #google-analytics.
#Amazon only stores your data, but #google-analytics knows your behavior. Everything about eulalie you: where did you stop by for a while, and where did you went after.
#diaspora #privacy #google #surveillance
I believe this video is via @{Chris ; teslas_moustache@diasp.org} http://www.youtube.com/watch?v=CP8CNp-vksc
#rms #stallman #freedom #ethics #ubuntu #gnu #linux #free-software #privacy #spyware
what are you doing?
changing the #mac #address before I connect to #wifi.
ah, you need #internet.
yes, I need to check in on #foursquare.
#privacy
Richard #Stallman (the father of #GNU) believes that #society by accepting overt full time #tracking implicates the innocent who don’t carry a #phone as a full time tracking device as suspicious.
It works like this: For some reason, maybe you were cheating on your wife and visiting a girlfriend or just playing D&D with your nerd buddies near what unknown to you turns out to be a meth lab. After the cops bust the lab they do an audit of cell tower records a few months back and find you visiting at strange hours in the same vicinity, you are now suspected of being a top level drug dealer who is lying low after the lab bust. The cops finally get tired of you not selling drugs after following you for a few weeks probably with a good search warrant to tap phones and sneak&peek your house. They break the door with a SWAT team, shoot your dog, pepper spray your wife, cuff your kids, and haul you in. The cops offer to drag you through court and maybe even lie to get a conviction unless you turn in more drug dealers, they also can confiscate your home, vehicle and posessions with only suspicion that it was used in smuggling or selling #drugs.
Kinda makes you wish you had not carried you standard issue human #tracker with you everywhere not knowing if there was something suspicious that you might get tangled up in.
More likely is situations like the Arab spring(summer,fall, winter, spring, summere…) where governments may direct secret police to monitor the #mobile phone #network logs to track people.
Bing tinfoil hat about #privacy is like being tinfoil hat about the law, you never know when you will be mistaken as a much bigger fish than you actually are. I used to be a SWAT team medic, the busts we made were sometimes ridiculous, the way the family of the suspect were often treated was even worse, so yea, I got issued a tin plated kevlar helmet.

#rms #freedom #democracy #privacy #interview #drm #obedience #free-software #surveillance http://www.newint.org/features/web-exclusive/2012/12/05/richard-stallman-interview/
Q Tell me about these malicious features.
There are three kinds: those that spy on the user, those that restrict the user, and back doors. Windows has all three. Microsoft can install software changes without asking permission. Flash Player has malicious features, as do most mobile phones.
‘Any change in the way protest is done is an opportunity for governments to criminalize it.’
Digital handcuffs are the most common malicious features. They restrict what you can do with the data in your own computer. Apple certainly has the digital handcuffs that are the tightest in history. The i-things, well, people found two spy features and Apple says it removed them and there might be more
When people don’t know about this issue they choose based on immediate convenience and nothing else. And therefore they can be herded into giving up their freedom by a combination of convenient features, pressure from institutions and the network effect. That’s why I focus now on spreading the awareness of the philosophy of free software and the issue of freedom that we’re fighting for. Because if you have some courage and you recognize the harm that they are doing, you can resist.
Q What do you think about the actions by hactivists Anonymous in defence of internet freedoms?
Well, their primary activity consists of a network protest where people send lots of request to a website. It’s the virtual equivalent to having a protest on the street in front of their office.
This is simply democracy. But we live in an age where governments that actually work for the banksters and other major businesses are trying to criminalize all forms of popular political activity. They look for clever ways to punish protests such as besieging protesters for hours. So any change in the way protest is done is an opportunity for them to criminalize it. If people used to protest in the street and now it’s in the network, well they can prohibit protesting in the network and call it an attack.
#privacy related talk on a slashdot #realityshow #ciq #carrieriq http://mobile.slashdot.org/comments.pl?sid=2553980&cid=38232678
#openmoko #surveillance #mobile #freedom
Christopher Soghoian, principal technologist at the ACLU’s Speech Privacy and Technology Project, said he was excited to see a company like #Silent-Circle visibly competing on #privacy and security but that he was waiting for it to go #open-source and be audited by independent #security experts before he would feel comfortable using it for sensitive #communications. http://www.slate.com/articles/technology/future_tense/2012/10/silent_circle_mike_janke_s_iphone_app_makes_encryption_easy_governments.single.html via @{Dr. Roy Schestowitz ; schestowitz@joindiaspora.com}
Chris Soghoian’s articles in aclu.org blog http://www.aclu.org/blog/author/chris-soghoian #analyst #freedom #freedom-of-speech #privacy #web #armenian #rights