
ես խնդիր ունեմ՝ ֆֆ֊ն եթէ փակուի, գիտի որ պատուհանը որ աշխատատիրոյթ տանի, իսկ փիջինը չի իմանում։
հետեւաբար ամէն անգամ փիջին անջատել միացնելուց յետոյ երկար դասաւորում եմ պատուհանները։
հիմա աւտոմատացրի էդ խնդիրը։
մի նիշքի մէջ ձեւակերպում եմ որ պատուհանը որ տիրոյթում լինի։ ցանկ ա, զի չգիտեմ որ տաբն ա էդ պահին բաց լինելու, ու ապա որն ա լինելու պատուհանի վերնագիրը։
սա իմ կարգաւորումների նիշքն ա՝
2:oberon spyurk khosenk մերգելեան գրադարան
2:intentionally_blank посторонним_в to_the_ocean_netters-dev ցանցառներ_նախագծում շեքսպ_արեւ_սոնա
3:#pine64 #pinetime #pinephone
3:#pinetab #pinebook
4:#ada #retro ##forth
4:#fpc #oberon #lazarus #pascal
5:#gentoo-powerpc #hellosystem #plan9 #minix #netbsd #freebsd #openbsd #gentoo
5:#maemo-leste #maemo #postmarketos #postmarketos-offtopic
6:#security #opsec
6:privacy-and-security privacy
7:dino_chat blabber_support conversations operators prosody xsf
7:##programming ##tokipona #pidgin #lesswrong
8:#socialhome #thefederation #diaspora #mastodon #scuttlebutt #indieweb
8:dishub fediverse disroot schroedingers_chat 404_English_chat support_for_chat.sum7.eu
9:#roms #ebooks
9:#tilderadio #helpdesk #anonradio
10:#soylent #politics #editorial
10:политика
11:fotografie
11:#photogeeks #darktable
11:#opensourcemusicians
11:cybersnoot
12:openhardware homebrew_server_club modding_fridays openwrt 64sprites
12:geminauts
13:onfoss floss linuxforum FSFE_community
13:#windowmaker #icewm
ամէն տիրոյթում ուզում եմ ունենալ երկու պատուհան, ու յստակ տեղում ու յստակ չափսի։
հիմա որ շրջում եմ տիրոյթներով, շատ հաճելի ա տեսնել նոյն ձեւ բաց պատուհաններ, ու խօսակցութիւնները։
սա էլ հիմնականում սկրիպտն ա՝
function find_active_tab_from_list2 {
read -a list <<< "$(printf "%s" "$@")"
local func_result=""
for i in "${list[@]}"
do
res=`wmctrl -l | grep ${i} | awk {' print $1 '}`
if [[ -n "$res" ]]
then
#func_result=$i
func_result=$res
fi
done
echo "$func_result"
}
այս ֆունկցիան վերնագրերի լիստն ա վերցնում ու գտնում window id֊ն որը պարունակում ա դրանցից մէկը։
(կարելի էր եւ window id չվերադարձնել, այլ հէնց անունն օգտագործել, բայց մտածեցի window id֊ն հաստատ չի կրկնուի)։
սա էլ մնացած սկրիպտի մասն ա՝
if [[ -z $1 ]]
then
echo "provide config file name"
exit
fi
set -x
var=0 #this is used to check for odd or not to put window on the left or right
while read line
do
wrkSpc=`echo $line | awk -F ":" {' print $1'}`
winLst=`echo $line | awk -F ":" {' print $2'}`
win=$(find_active_tab_from_list2 "${winLst[@]}")
if [ $((var%2)) -eq 0 ]
then
wmctrl -i -r $win -t $wrkSpc
wmctrl -i -r $win -e 0,150,50,800,900
else
wmctrl -i -r $win -t $wrkSpc
wmctrl -i -r $win -e 0,1050,50,800,900
fi
var=$((var+1))
done < $1
նախ ստուգում ա արդեօք կարգաւորումներով ֆայլի անունն ա ստացել, յետոյ տող առ տող առանձնացնում ա տիրոյթը տաբերի անունների ցանկից։
կանչում ա էն ֆունկցիան, ստանում ա պատուհանի համարը ու տեղաւորում այն էն կոորդինատներով որ նշած են։ յաջորդ անգամ միւս կոորդինատներով ա տեղաւորում։
կարելի ա էլի լաւացնել, որ ըստ էկրանի չափսերի աւտոմատ որոշի ոնց տեղաւորի։ դէ ըստ իմ նախընտրութիւնների, ես օդ եմ սիրում, ազատ տարածք այդ պատուհանների միջեւ եւ շուրջը։
սա էլ սկրիպտով պանակը։
#սկրիպտ #էքս #իքս #էքսորգ #իքսորգ #լինուքս #իւնիքս #փիջին #պատուհան #չաթ #էկրանահան
interesting, win10 during setup tells you “create a super memorable password”, doesn’t tell “create a super unbrutforcable password” or something more security oriented. because super memorable is an alias to easily breakable, right? probably. (:
#microsoft #security #password #windows10 #usability #privacy
“UNIX Security” is an oxymoron.
http://phrack.org/issues/7/7.html ((:
#history #vintage #unix #security #archive
would like to write about protonmail.ch or protonmail.com
It might look like I am criticizing the project, while I do not. Apparently I have even donated them money.
Recently they’ve opened free registration, so you can get your protonmail.com address. Actually I do not understand why sometimes you get protonmail.com and sometimes protonmail.ch domain. Your username @ protonmail.com does not work as username@protonmail.ch and vice versa.
So, protonmail claims that they encrypt your mailbox, and only you can decrypt it. You need to have two passwords - first for the login, and second to decrypt the mailbox. If you happen to forget the second password, then your mailbox will be lost forever, you can create a new mailbox and encrypt it with different password.
It all seems very attractive, however there are questions:
— if the mailbox is encrypted, then when you receive the email, they cannot put it to the mailbox? Then they have to store it at some temporary location? Wait until you login to decrypt the mailbox, so that they can add the email to that mailbox while it’s temporarily decrypted?
— if there is such a state, then if they required to retrieve your emails, they can do that technically, when you are logged in? and when you are not logged in, they can make copies (again, technically) of your emails while they were not added to your mailbox?
— if you send emails to the other email provider, like google, then obviously, your email will be stored and never erased by google. that is why Protonmail suggests to send emails from proton to proton in order to stay safe.
#protonmail #mail #security #cryptography #privacy
there were one network administrator, and he was saying than he is frustrated that Armenia did not ban free wifi spots. when i’ve asked why, he answered that there is a lot of crime happening because of free wifi spots, and he gets a lot of requests, even got request from interpol.
well, i believe it’s a way of thinking of policeman, not system administrator.
policeman wants to simplify it’s work, and putting everyone to cell they can decrease the probability of crime. by banning open windows they can decrease probability that some thief can use them. but it’s not a way of thinking of administrator. well, i believe it should not be.
when i came to work where i work now, i’ve learned a sentence from my colleagues: “we are not police, we are administrators.” i like it a lot.
#police #surveillance #network #safety #security #wifi #freedom
here was a ted talk, i believe, and one guy from Sweden was saying - if somebody is watching me, i would prefer it to be local NSA, rather than US NSA.
Well, I envy him. He trusts local NSA so much. He believes that it’s not engaged in crime, corruption, unlawful activities. At least, it’s likely engaged less than the NSA of my country. Thus he feels himself more confident than me.
I am afraid of my local NSA more than of wolves, vampires, ghosts. It’s not they who might nock my door at 5am, when I am completely innocent. And definitely not US NSA. It’s my native, lovely, NSA. Which supposedly defends interests of the nation, but I am not quite sure it does not actually defend interests of other parties like their own, government, criminals instead. Sigh.
#safety #naive #sweden #nsa #privacy #surveillance #corruption #crime #confidence #security #freedom
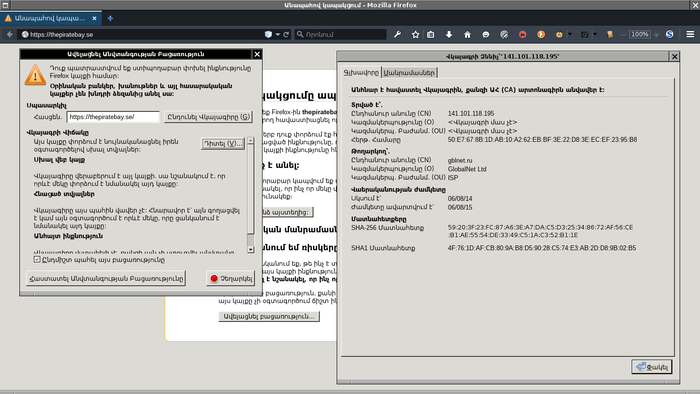
connecting to the piratebay from my hotel wifi. it asks to accept a self signed certificate issued by gibnet.ru. of course i did not, instead, via tor it did not require to accept any unknown certificate. if i would accept it they would be able to intercept my traffic. (:
#russia #security #privacy #thepiratebay #ssl #https #crypto #intercept #screenshot #freedom
The Half-Baked Security Of Our ‘Internet of Things’ http://www.forbes.com/sites/kashmirhill/2014/05/27/article-may-scare-you-away-from-internet-of-things/
I know one of these guys (:
#internet #security #surveillance #internet-of-things #camera #armenian
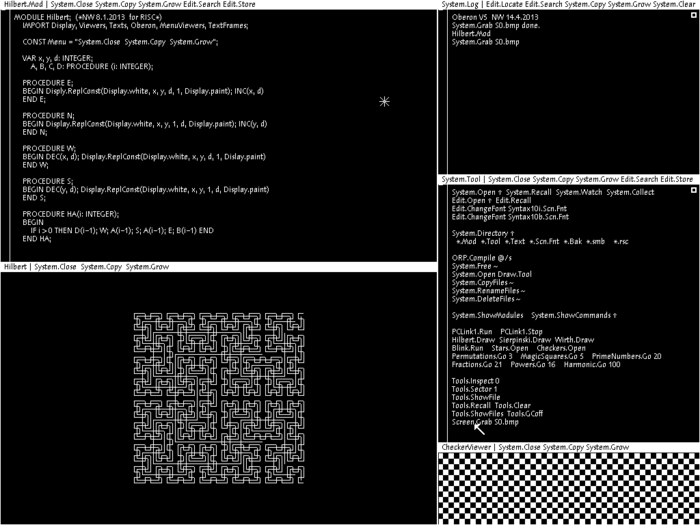
New edition of Wirth’s book Project Oberon is out. It describes not only built from scratch software(entire operating system and compiler), but design of the hardware as well.
The vast complexity of popular operating systems makes them not only obscure, but also provides opportunities for “back doors”. They allow external agents to introduce spies and devils unnoticed by the user, making the system attackable and corruptible. The only safe remedy is to build a safe system anew from scratch.
http://www.inf.ethz.ch/personal/wirth/ProjectOberon/index.html
#oberon #wirth #niklaus-wirth #risc #programming #fpga #books #programming-languages #compilers #operating-systems #compiler #freedom #design #security #privacy #surveillance #reliability
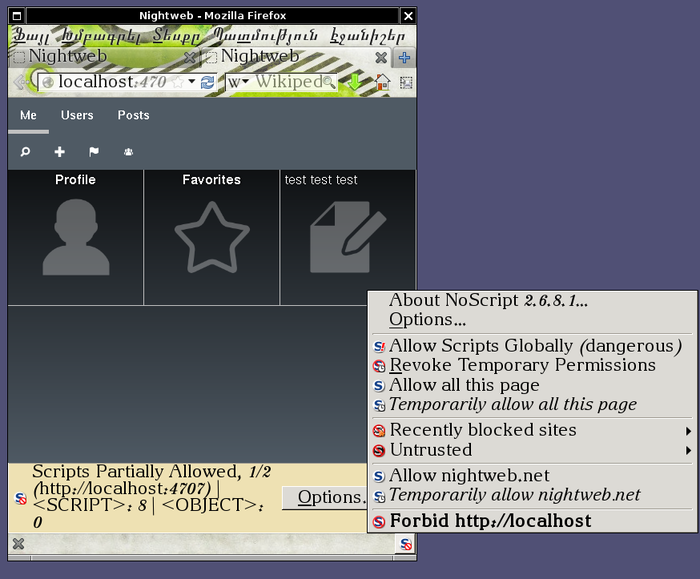
am I right that #nightweb is using #java-script loaded from nightweb.net? Then if nightweb.net gets hacked all the clients will be affected. Would like it to load #js locally, from the local file system.
#security #privacy #net #internet

“Whatever you put out I’m gonna buy it, so what’s your latest? I wanna try it” So what is the next #marketing #buzzword in #security ? I declare #2013 to be the year of #Intelligence
http://blogs.rsa.com/the-next-marketing-buzzword-in-security-is/
Christopher Soghoian, principal technologist at the ACLU’s Speech Privacy and Technology Project, said he was excited to see a company like #Silent-Circle visibly competing on #privacy and security but that he was waiting for it to go #open-source and be audited by independent #security experts before he would feel comfortable using it for sensitive #communications. http://www.slate.com/articles/technology/future_tense/2012/10/silent_circle_mike_janke_s_iphone_app_makes_encryption_easy_governments.single.html via @{Dr. Roy Schestowitz ; schestowitz@joindiaspora.com}