In order to allow concatenation of strings to be efficient in both time and space, it must be possible for the result to share much of the data structure with its arguments. This implies that fully manual storage management (e.g. based on explicit malloc/free) is impractical. (It can be argued that this is true even with conventional string representations. Manual storage management typically results in much needless string copying.) Though an explicitly reference counted implementation can be built, we will assume automatic garbage collection.
https://www.cs.rit.edu/usr/local/pub/jeh/courses/QUARTERS/FP/Labs/CedarRope/rope-paper.pdf
#paper #string #strings #rope #gc #storage
Social media have provided instrumental means of communication in many recent political protests. The efficiency of online networks in disseminating timely information has been praised by many commentators; at the same time, users are often derided as “slacktivists” because of the shallow commitment involved in clicking a forwarding button. Here we consider the role of these peripheral online participants, the immense majority of users who surround the small epicenter of protests, representing layers of diminishing online activity around the committed minority. We analyze three datasets tracking protest communication in different languages and political contexts through the social media platform Twitter and employ a network decomposition technique to examine their hierarchical structure. We provide consistent evidence that peripheral participants are critical in increasing the reach of protest messages and generating online content at levels that are comparable to core participants. Although committed minorities may constitute the heart of protest movements, our results suggest that their success in maximizing the number of online citizens exposed to protest messages depends, at least in part, on activating the critical periphery. Peripheral users are less active on a per capita basis, but their power lies in their numbers: their aggregate contribution to the spread of protest messages is comparable in magnitude to that of core participants. An analysis of two other datasets unrelated to mass protests strengthens our interpretation that core-periphery dynamics are characteristically important in the context of collective action events. Theoretical models of diffusion in social networks would benefit from increased attention to the role of peripheral nodes in the propagation of information and behavior.
The Critical Periphery in the Growth of Social Protests
via @{Արգելիոն Argelion ; aragev@spyurk.am}
#paper #protest #twitter #social_media #internet #research
i am reading a paper about making a kernel which supports cooperative multitasking, to replace the current A2 kernel which supports more wide spread blocking synchronization. i wonder if they’ve managed to change the kernel and if current A2 has this lock free kernel or not. i remember i have read something about problems they had with drivers - they need to be rewritten to not use interrupts any more.
#multitasking #cooperative_multitasking #theses #paper #a2 #oberon #operating_systems #blocking_synchronization #preemptive_multitasking #parallelism #programming

it says “no beer”.
the old armenian joke was related to empty petrol stations of 80ies. one comes to the petrol station and sees a paper stating “no petrol at all”. he asks, why did they write this “at all”? they answer, because every person who comes asks us - “no petrol at all?”.
so they had to write “no beer at all” (:
#saint-petersburg #petersburg #petrol #shortage #beer #text #inscription #paper #city #street #photo
Jig’s series of questions are strongly gender-marked. She uses a proportionately large number of tag-end questions: “wasn’t it?”, “isn’t it?” (Dietrich). She also uses circular and vaguely generalized evaluations of their activities rather than direct statementns— “that’s all we do”— the goal of her conversation being consensus.
Gender-linked Miscommunication in ‘Hills Like White Elephants’ http://www.csus.edu/indiv/m/maddendw/Hem_fem.pdf by Pamela Smiley from University of Wisconsin
#paper #gender #communication #talk #hamingway #consensus
it is an old paper and I like it a lot.
A Comparison of Ada and Pascal in an Introductory Computer Science Course http://www.sigada.org/conf/sa98/papers/murtagh.pdf
#ada #pascal #programming #teaching #education #computer_science #paper
Operating systems verification http://ssrg.nicta.com.au/publications/papers/Klein_09.abstract
#operating_systems #os #programming #verification #paper
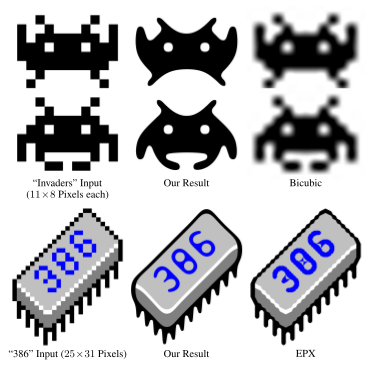
Depixelizing pixel art
#research #pixelart #depixelization #science #paper #art
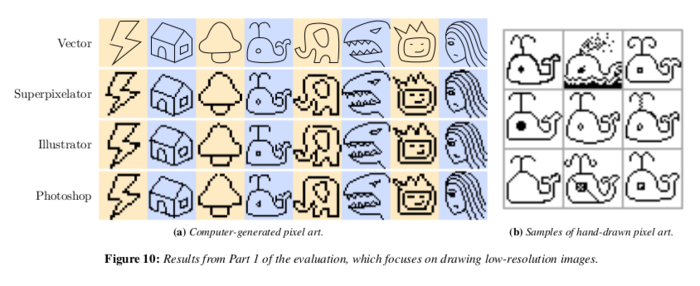
Rasterizing and Antialiasing Vector Line Art in the Pixel Art Style
site | paper | youtube demo
#pixelart #raster #rasterization #pixel #algorithm #research #paper #video #science #art
this app uses ANS synthesizer՝ musical instument, which Yevgeni Murzin designed in1937֊1957 years
http://www.youtube.com/watch?v=lzoVnqLy29U
#android #ANS #app #software #music #audio #recorder #paper
via @{sense ∇ ; sense@diasp.org}
Lightweight parametric polymorphism for Oberon.
http://research.microsoft.com/en-us/um/people/cszypers/pub/jmlc97.pdf
#oberon #oberon-2 #polymorphism #programming #research #paper #oop #development #software
I was thinking, that single space os should have weak security, but it seems I was wrong. This is a very interesting paper -Sharing and Protection in a Single Address Space Operating System
This paper explores memory shanig and protection support in Opal, a single address space operating system designed for wide address archtectures. Opal threads execute within protection domains in a single shared virtual address space. Sharing is simplified, because addresses are context-independent.
http://homes.cs.washington.edu/~levy/opal/opal-tocs.pdf
#operating-systems #opal #paper #protection #a#####

Վոլֆգանգ֊Թիլիմանս թուղթ կաթիլ Wolfgang-Tillmans paper drop
#photography #photo #art #paper #drop #ֆոտո #լուսանկարներ #արվեստ #կաթիլ #թուղթ ##
#Վոլֆգանգ֊Թիլիմանս #Wolfgang-Tillmans

Old #paper, but I like it. #Bruce-Perens: Analyzing #Microsoft ’s #TomTom #Lawsuit
#software-patents